Danger, Deception, and Fraud: Exploring the Vicious World of Online Scams
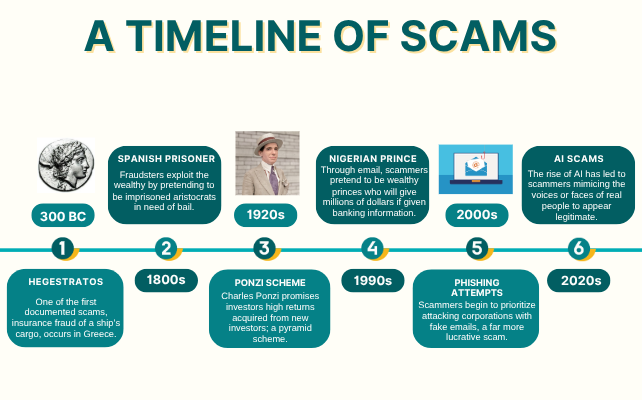
Centuries ago, around 300 BC, a shipping merchant named Hegestratos tried to swindle insurers by sinking his ship, but kept the cargo for the purpose of claiming money on account of a pretended loss. Although it may be somewhat rudimentary by today’s standards, Hegestratos’s attempt highlighted an aspect of human nature that has remained constant throughout the ages: the willingness to manipulate others for personal gain. Over time, scams have evolved to exploit every little technological and societal development, increasing in scope and advancing in sophistication.
Before the invention of the Internet, scams largely depended on pure deception. Common methods included forging signatures, altering documents, and impersonation. The “Spanish Prisoner” scam, in which fraudsters posed as wealthy nobility imprisoned in Spain and needed money for their release, was one popular method of deception in the early 19th century.
The Industrial Revolution marked the beginning of the rise of rapid technological development and urbanization, creating an even greater opportunity for new scams to form. Known as the “Ponzi Scheme,” named after the 1920s swindler Charles Ponzi, the ploy promised high returns on investments but relied on funds from new investors to pay previous ones, fabricating the image of profitability where, in fact, there was little to no legitimate financial gain. This scheme followed the invention of the telegraph and later the telephone, which scammers could utilize to reach their targets and conduct operations over long distances.
With the birth of the Internet, however, scams entered an entirely different era. Phishing emails, designed to appear to come from a trusted source like America Online or a bank — to steal sensitive information, became increasingly common throughout the 1990s. Such deceptive emails could trick users into revealing personal information, like credit card numbers and passwords. For example, the modern version of the Spanish Prisoner scam — the Nigerian Prince scam — utilized emails to reach and extract information from victims, promising vast wealth in exchange for upfront payments while posing as an allegedly wronged and robbed Nigerian aristocrat.
With the growth of e-commerce, online scams also started to become more prevalent, with fake websites, counterfeit products, and fraudulent sellers beginning to appear everywhere. Cases of identity theft also began to rise as scammers took advantage of weak cybersecurity systems to obtain personal and financial data. Malware and ransomware, which are when hackers hold sensitive data hostage and demand ransom for their release, also became new threats.
Since the 2010s, social media has been a major platform for scams, and fake profiles, phishing links, and scam advertisements have become popular methods to attract victims and acquire their personal information. Online dating frauds, lottery scams, and even fake job offers began to thrive. Additionally, crowdfunding platforms like GoFundMe, which were intended to support genuine causes, had turned into breeding grounds for fraudulent campaigns that preyed on public generosity.
While scams have always been difficult to detect, the recent rise of AI revolutionized the way these schemes are carried out. Deepfake technology allows scammers to create extremely realistic audio or video impersonations of public figures or trusted individuals, such as family members. These deepfakes can be used to trick victims into believing they are talking to someone they know or trust when in reality, they are being manipulated into revealing sensitive information.
Scams have been evolving over several centuries, becoming more complex and harder to identify. From early cons like the “Spanish Prisoner” scam to the use of AI and deep fakes, scammers continually find new ways to deceive others. Ultimately, as technology continues to evolve, the methods scammers use inevitably will, too.
“Hey, I created this for you on Instagram.”
Despite its innocuous appearance, this message can wholly consume your Instagram in a matter of moments. As soon as you click the attached link and login to see the elusive “creation,” you unknowingly share your username and password with strangers on the internet. Soon after, you’ll lose control of your account, watching from afar as strangers direct message everyone you follow to pass along the same scam. Maybe you can change your password to make it stop. If not, you’ll be left with no other option than to vacate the account entirely.
This one message is a common example of phishing in our daily lives. Phishing, the act of cybercriminals sending scam messages to trick users into sharing personal information such as login credentials or bank account information, permeates virtually all internet platforms. In cases of phishing, cybercriminals usually attach corrupted links to their scam messages, which can download malware onto a user’s computer or leak their personal data. By clicking on attached phishing links, users risk losing power over their accounts or, worse, being a victim to identity theft or financial fraud.
While the consequences of phishing are grave, phishing utilizes simple tactics to lure in users. To get users to open a scam message, cybercriminals try to base their scams around something of interest to their targets. This can mean sending messages as a popular brand or app (like Instagram) that users enjoy and use. When an individual sees a message from a familiar company, they are much more inclined to open it. Furthermore, scammers tend to instill a feeling of urgency in their messages. They might say that if you don’t open an attached link immediately or within a specific time frame, some bad consequence will follow. This can range from an order being cancelled, a subscription being terminated, or a financial transaction being scratched. To persuade even more users to click a link or reveal their information, cybercriminals often dangle free promotions. Typically, scammers might offer a discount or free item, or they might state that a user won an obscure contest.
Spear-phishing implements these tactics against one particular individual. This pointed scam often is more convincing and dangerous than generic phishing, as cybercriminals harness personal information about their victim to make the scam more alluring. They might address the victim by name in communications or guise themselves as the company the target interacts with most.
Despite phishing’s reliance on modern social media and forms of communication, phishing is not that new. The first recorded instance of phishing took place in 1994 when a teenager created a Windows application to crack American Online (AOL) accounts. After stealing users’ login information and posing as customer service, the teen gained control of a multitude of other accounts. Since then, cases of phishing have only expanded in terms of size and casualties. In 2009’s Operation Phish Phry, cybercriminals in the US and Egypt stole hundreds of account holders’ financial information, transferring $1.5 million into their own account. Following Phish Phry in 2014, cybercriminals stole 100 terabytes of confidential data by impersonating colleagues of higher-ups at Sony Pictures. As a result of this breach, Sony lost $100 million. Similarly, Facebook and Google also lost $100 million after a 50-year-old pretended to be their business associate, Quanta Computer. Through fake emails, invoices, and contracts, the scammer stole money.
Phishing is ultimately incredibly common, both among ordinary people and large corporations. Although phishing can severely harm its targets, it can easily be avoided with a cautious eye. Staying wary of generic greetings, odd phrasing, misspellings, or inconsistencies within a sender’s name can help you avoid any scam messages. Spam filters can aid in removing communications from cybercriminals in your inbox, but they’re never entirely effective. To best avoid fishing, look into security software, avoid using the same password for different accounts, and most importantly, think critically about what you open.
Voice cloning, deepfakes, and impersonating – these are all ways cybercriminals are using AI to trick people online. With the increased popularity of artificial intelligence, scammers are abusing its positive qualities and using it for the worse.
When it comes to cyber scams, most people have gotten a good grasp of what is real, and what is fake. Cyber scams could come as texts from scammers acting as postal service workers about a missing package, recruiters offering a job opportunity, or companies introducing a new contest. These texts instruct people to click a link for further information which hacks their device, allowing the scammer to dig deeper into their information. Since scammers have been using this same old text scam tactic all these years, most people have educated themselves on determining which texts from unknown numbers are suspicious and should be ignored. Consequently, the success of scammers has been hindered, leading them to seek other ways to trick victims.
Fortunately for the scammers, AI has been an incredible resource when it comes to misleading society. AI utilizes computers and machines to imitate the way humans think, respond, and learn, but in a quicker fashion. Nowadays, scammers have gotten a hold of AI technology that can not only imitate the voices of people, but can also create fake videos of them. These scamming techniques are called voice cloning and deepfakes.
AI can voice-clone people with the help of social media. Scammers will stalk people’s social media to find as little as a three-second video of them speaking. After putting this recording into AI, the robots can say anything in almost the same way the real person would speak.
Deepfakes are AI-replicated photos or videos. Videos incorporate voice-cloning to imitate a person saying something. The high-tech robots in the AI machines can replicate a video of a person to look and sound exactly the same as they do in real life which can more easily mislead people.
With AI in scams, cybercriminals are using voice-cloning and deepfakes to imitate a person urgently calling a relative, requesting money immediately through systems such as Bitcoin, other payment apps, or direct bank account transfers. Since voice-cloning makes a robot sound exactly like a real person, the relatives believe the call is legitimate and go through with the money transfer, causing them to lose tremendous amounts of money.
For example, last year in Brooklyn, a couple, Robin and Steve, were asleep and were awoken by Steve’s mother calling in the middle of the night. She was in a state of panic, and the line switched to a man threatening to kill her if Robin and Steve didn’t do exactly what he requested. The man demanded five hundred dollars for travel, to be sent through Venmo. The couple paid the money, not realizing they were scammed through voice-cloning until after the payment was completed.
Although it is becoming harder and harder to detect scams now that AI is in use, research suggests that there are some ways to identify when video or audio is AI. Key signs that an audio is AI are when the caller seems to be in a panic, they are requesting money urgently so the victim doesn’t have time to think, they are threatening to hurt others if their request isn’t carried out, and they are requesting a secret online transfer of money. Some signals that a video might be AI are if the video has jerky movements, there are changes in skin tone/texture around the eyes, unusual blinking or hair movements, or uncharacteristic word choice for the person. If people keep these key signals in mind when receiving strange, urgent calls or messages, they can more easily detect the authenticity of the person calling.
It’s also important to note that a bank will never call someone for important information regarding their account. These types of conversations will only be held in person, so if someone is calling someone for bank information, it’s most likely a scam.
Overall, the use of AI in impersonations has taken the scam world for a turn. Cybercriminals are looking to prey on innocent people using these high-tech skills, hoping to guilt trick them into handing over money with an impersonation of family and friends. Scammers also tend to target the older generation with these types of scams, knowing that they have less knowledge about technology and its abilities. People should warn their loved ones about this issue to prevent them from falling for misleading impersonations.
Knowing these things, people must keep their eyes peeled for potential AI in online scams.
“It can’t happen to me, right?”
This is the sentiment expressed by most people regarding online scams. They believe that only idiots fall for them, and anyone with even a shred of critical thinking skills can see right through these futile attempts. However, both the national data and personal experiences paint a different picture. According to the Federal Trade Commission (FTC), 2023 saw over 2.6 million reports of fraud, amounting to over 1% of the adult population. Around 38% of Americans have been scammed at some point in their lifetime, and despite awareness campaigns, this number is still growing.
On a local scale, Cherry Hill High School East has dealt with many online scams. Specifically, students are often targeted by scams to give up information for their online accounts, which then spreads to other students via social media. This cycle can have devastating consequences for students affected. One such student, Lukas Ortega (‘26), gave his personal account of falling victim to an online scam.
“Some random person DMed me on Instagram, and they said, ‘Can you help me sign back into my account?’” said Ortega. “And since I don’t really know how Instagram works, I said ‘Yeah, sure.’”
These types of scams appear benign at first, and appeal to the trustworthiness of the victim. By asking them to help out, the scammer encourages the victim to follow their instructions, making them feel like a good person for complying. The victim’s guard is let down, leading to lapses in jugdement.
“I gave them my number, and then they said, ‘Send me the verification code.’ So I sent the code, and then I realized I was locked out of my account.”
Scammers often find clever ways to deceive their victims. By claiming that the verification code exists as a pesky obstacle, or as a way to ensure the victim’s own credbility, the scammer prevents the victim from realizing the true power dynamic at play. By the time the seeds of doubt are sown, though, it is often too late.
“I lost the account. And they messaged a bunch of people on the account to try and scam them as well.”
Perhaps the most dangerous part of these scams is how they spread to others like a plague. Once one person falls victim, the amount of people exposed to the scammer will exponentially increase. Similar to how East students always seem to get the flu in droves, their connections cause online scams to affect each other in sudden waves. Another student also was a victim of the same scam Ortega fell for, instantly doubling the threat.
To break free from this cycle of scams, Ortega has some advice that he wishes others would follow:
“Make sure you know the person that you’re talking to… and if you’re suspicious of them, ask something only they would know.”
By taking a few simple precautions, East students can remain significantly safer online. The easiest step is to naturally be suspicious of anyone asking for any of your information. Remember to always request specific reasons for sharing information, and if you’re still suspicious, just don’t send it. It’s far easier to talk in-person to clarify, and if you don’t know the person well enough to see them in person, there’s no reason they should need your information anyway. So, when the next batch of scammers try to infiltrate East’s halls, keep them out with your superior logic and precautions.