Danger Lurks in Our Screens: Cyberwarfare and Cybersecurity
February 26, 2023
In the Age of Information, our world has steadily become immersed by technology, whether it be the vast landscape of social media or the limitless bounds of the internet. But with this immersion comes risk – the cyber realm today is privy to innumerable threats. Whether it be government sponsored hackers or malware, the cyber world is one riddled with potential dangers. Read, watch and play along with Eastside as we take a deep dive to explore these issues.
United States Cyber Command
Recent cyberattacks have revealed our vulnerability
Espionage and information acquisition have been major aspects of international relations since humans first put pen to paper. And yet, with the boom in technology experienced in the last few decades, the ability of nations to spy on their neighbors and attain hordes of knowledge has skyrocketed upwards. And, crucially, it is not only governments but rogue groups and criminal organizations that now also possess the ability to harness the power of the internet.
On a national scale, the American people of the 21st century have borne the brunt of this skyrocketing, as part of a larger global population with exponentially increasing access to the internet. Today, the United States numbers among the top 20 countries in the world in terms of the number of cyberattacks it suffers yearly.
Worse still, cyberattacks are hardly ever limited to only governmental or military targets. Rather, as the aim in most breaches is to steal and secure as much data as possible and then proceed to sell or ransom that data, major cyberattacks in recent years have been striking civilian areas and infrastructure much more often.
The most recent, and perhaps the most significant example of this occurred on May 7, 2021, with the Colonial Pipeline ransomware attacks. The Colonial Pipeline, an oil transmission system delivering oil to large portions of the country, began to experience serious issues with its digital monitoring and management systems. The perpetrators were soon discovered to be the cybercriminal group DarkSide, who demanded nearly 5 million dollars worth of ransom money from the Colonial Pipeline Company. Already having been forced to put a pause on the operation of the pipeline as a result of the DarkSide disruption, the company agreed to pay the ransom. By May 9, the company had successfully negotiated with the cybercriminals and begun to restore its functionality. But in the meantime, a mass gas and fuel shortage had occurred. It took executive orders, declarations of emergency and the contributions of US senators to finally stem the tide of the shortage. The Colonial Pipeline attacks greatly underscored the United States’ need to develop substantial, rapid and effective infrastructural cyber attack response.
And yet this wasn’t the first, nor the only time the United States suffered such a large scale cyber attack of this sort. In 2013, Yahoo reported that their servers had been breached and up to 3 billion users’ personal information put at risk by hackers seeking to sell off said information. Throughout the 2010s, Apple and its subsequent products and services were affected by a series of breaches and exploits, aimed at attaining sensitive user information. And, famously in 2019, the software company SolarWinds was breached by attackers of malicious intent who proceeded to lay hands on extremely sensitive information regarding clients of SolarWinds – including clients like the Department of Homeland Security.
Substantial numbers of these attacks are perpetrated by groups of hackers who are sponsored or tolerated by modern governments. That is not to say that said governments themselves are not capable of launching their own cyber attacks. Among the countries with the most developed cyberwarfare programs in the world are such oft-belligerent names such as China, Russia and even the United States.
Citizens of the world have a foreboding future with relation to the cyber world ahead of them. Only time will tell what changes may arise in the future, but for now, the cyber domain remains a dangerous plain.
The history of cybercrime frightens

Robert T. Morris, the creator of the Morris worm, one of the internet’s first malwares.
Throughout history, one of the biggest developments of society was the advancement of technology. Most notably, the creation of the world wide web in the late 1900s was one of technology’s most major strides. Among the greatest conveniences that followed the introduction of the internet is our ability to “Google” any question we have and the beginning of new Artificial Intelligence platforms such as ChatGPT providing answers we need within seconds. Despite these benefits, what risks are we taking with this ground-breaking development?
The use of cyberspace can be detrimental to us through the increase in cyberwarfare and cybercrime. While the internet was invented in the late 1900s, it is significant to recognize the early uses of espionage technology. During World War II, Nazi Germany was able to use a point of origin to communicate using radio signals in which German bombers were able to fly throughout continental Europe to Great Britain during the Battle of the Beams. This was used as a way to know when their targets were within reach. Another way that belligerent powers were able to use radio frequencies was during the early 1900s where other nations would intercept them in order to gain intel on the location of the opposing countries.
As technology developed via the formation of the internet, there were more incidents that pointed towards the intent of taking private information. This includes the 1994 “Rome Lab incident” in which a “sniffer”, entailing an unknown wiretap program, was discovered on the US Air Force’s development network. Attackers were able to steal the user names and passwords of the workers at the Rome Laboratory in New York. From this attack, an anonymous person who went by “Kuji” and a 16-year-old located in the United Kingdom were able to gain access to secret defense research projects and seize information that was kept on the computers of the Korean Atomic Research Institute among other crucial information hubs.
In 1988, there was also the creation of the Internet Worm which was spread throughout the Internet and was known to have destructive impacts to computers that were using the Internet during the same period of time. The worm was one of the first ever malware systems to exist and be able to spread to other computers. Such a worm was created by Robert T. Morris, hence the phenomenon was named the Morris Worm. Morris explained that such destruction was not supposed to occur and that the Worm was made to be harmless. However, a malfunction caused it to have such an impact. It is theorized that 6000 computers were impacted by this Worm, many of which belonged to the Pentagon, MIT, and NASA. Becoming aware that such incidents could happen, there was the creation of the Computer Emergency Response Team by the US government, with the mission of improving the protection of softwares and networks. Thus, aspects such as warnings, analysis, and solutions that would further improve networks and softwares to be less prone to incidents such as the use of the Worm began to be implemented.
As the age of technology continues to grow, we are not only faced with the increased comfort of doing tasks quicker, but the dangerous outlooks that follow. Everyday we face the risk of the influence of cyberattacks no matter how much protection may be improved. It is fundamental that we recognize such benefits and dangers as we grow with the adoption of technology now and in the future. It has always been so.
Cybercriminals attacked Cherry Hill
Created with Collage Maker, images courtesy of BitLyft and Wikimedia
Cyberattacks have not left Cherry Hill untouched, as the 2019 Ryuk ransomware attacks showed.
Locally, the threat of cyber attacks has remained present. In 2019, staff and students of the Cherry Hill School District struggled to access their emails and google drive. Some files were corrupted, and displayed the mysterious title, “Ryuk”.
This title is associated with a Russian cybercriminal organization. According to the New Jersey Cybersecurity and Communications Integration Cell (NJCCIC), Ryuk uses Emotet and TrickBot trojans to infect new systems and corrupt their data. This data is then held for ransom.
Estimates from cybersecurity experts place Ryuks’ total ransom earnings at $150 million since their emergence in 2018. At the time of the attacks in Cherry Hill, this number had only reached $3.7 million. Many school districts were impacted by Ryuk, as well as popular online schooling company K12. In 2020, an undisclosed sum was paid to Ryuk to prevent a data leak. At the time of these attacks, Cherry Hill was just a small part of the 500 US schools affected.
The Ryuk data outage lasted from October 4th to the 10th. During this time, a 15 member team of district technology employees and outside experts worked to solve the issue. However, not much else is known about the incident.
“There’s not a whole lot of information or specifics that I can share,” said Superintendent Joseph Meloche at a school board meeting. “Most of our systems are back up and running.” To improve security, the district has since transitioned to two-factor authentication and cloud-based email services.
While this seems to be the most notable instance of cyber instability within the district, it is certainly not the only one. Back in 2007, one student and one East alumni were accused of hacking into protected computers. According to reports, they altered the grades of themselves and four other students.
Given these instances of cyber attacks, it’s important to always exercise internet safety. To learn more about how to protect your data online, NJCCIC and the Cybersecurity and Infrastructure Security Agency (CISA) are helpful resources.
How well do you know your cybersecurity and technology history?
Try your knowledge with Eastside!
Loading…
Meet the technology prodigy who hacked our high school

Cherry Hill East alum Conrad Kramer developed Apple Shortcuts before the age of 19
Imagine you are roaming the halls of your high school, scrolling through pictures on Instagram, and out of nowhere, every single picture becomes the very same picture of a goat.
Conrad Kramer (‘14) pulled this exact prank nearly a decade ago during his time at Cherry Hill East. Kramer utilized his advanced technical abilities in multiple such endeavors throughout his time at East, always with humorous intentions. Since then, Kramer has stopped using his technological gifts to pull pranks and is now a software engineer and technologist.
Kramer developed his love for technology at a young age, helping his father repair broken computers bought off of Craigslist. From there, Kramer acquired a taste for programming and started to develop programs on his phone, even creating a system that automatically texted him the weather every day. This was before specific mobile applications for weather reports, making Kramer’s innovation groundbreaking.
“I basically learned everything I know about programming from the internet and from Youtube,” said Kramer. “I had a lot of friends on IRC – which is an old chat protocol that I used – and asked them programming questions and they would help me, so I kind of learned that way.”
Kramer continued to gain more programming knowledge throughout high school, eventually receiving acceptance into the billionaire entrepreneur Robert Thiel’s competitive THIEL Fellowship. This program is for students who do not want to go through the traditional educational route of college. The 20 to 30 people accepted into the THIEL fellowship every year are not allowed to attend college for the program’s two-year duration and receive $100,000 to start or build upon their innovative ventures.
While completing the fellowship, Kramer moved to San Francisco, CA, and started a company with a group of friends, which they maintained for about three and a half years. Working for the company, Kramer created Workflow, a mobile app that integrates other mobile applications in order to organize tasks. In 2017, Workflow was acquired by Apple, which renamed it as Apple Shortcuts. In 2015, Workflow won the Apple Design Award. When Apple bought their company, Kramer and his two teammates, Ari Weinstein and Nick Frey joined the Apple team.
Recently, Kramer decided to move on from his position as a software engineering manager at Apple and take a break from the inflexibility of working for a corporation. By his own admission, Kramer dislikes working for “the man” and prefers building software and being his own employer.
“Everyone thinks Apple does this or Apple does that, but Apple doesn’t do anything,” said Kramer. “People at Apple do all these things.”
Kramer is currently attending the Technology and Public Purpose (TAPP) Fellowship at Harvard, which trains its participants to use technology to make progress in public policy through individual projects. Kramers’s research for the duration of the fellowship centers around solar energy and how to make solar energy more affordable. After finishing the fellowship, Kramer plans on starting a new technology company.
Reflecting on his past 10 years in the technology industry, Kramer believes that a good mentor is extremely beneficial to those looking to dive into the field. He also thinks that those looking to enter the industry need to truly understand what they want out of their work. For some, working at a huge tech conglomerate is the dream of a lifetime, while others simply want to fulfill their passions through coding. With the number of tech companies dominating the industry, Kramer also believes that engineers need to think hard about their morals. Kramer believes while you can always get a new job, it is hard to recover your morals.
For Kramer, the most important concept for aspiring engineers to understand is that if they want to learn something, they can.
“If there’s anything you want to learn, you can at least get started on the internet,” said Kramer.
Although college may lead to success for some, Kramer had the motivation as a kid to take his learning into his own hands, which has allowed him to go from pulling pranks on his fellow classmates to developing an app on every iPhone today.
Eastside interviews Conrad Kramer
Eastside recently interviewed technology prodigy Conrad Kramer. As detailed in the article above, Kramer is notorious for exploiting his school’s network to pull off pranks and stunts. Watch along as Kramer recounts what came before, during and after in an interview with editors Enis Ercan and Lauren Winslow.
How can the average person protect themselves?
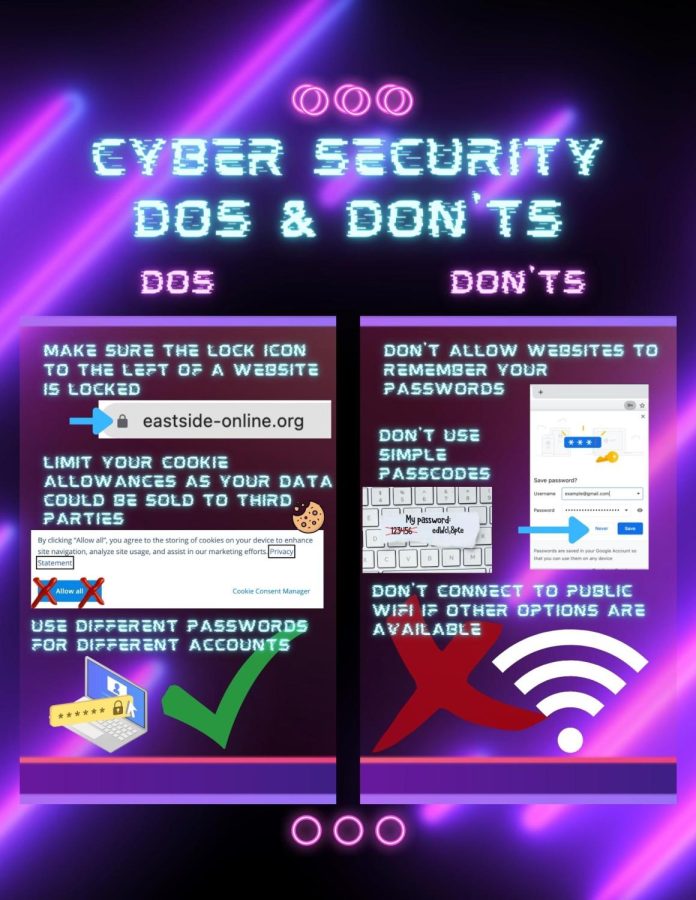
It may get overwhelming at times when attempting to implement various cybersecurity measures. Below are a few ways to protect yourself, so that your systems, networks and devices are fully secure.
- Create strong passwords. Longer passwords (at least 12 characters) are stronger. Use not only letters, but a variety of lowercase and uppercase letters, numbers and special characters. Use different passwords for each app/website.
- Be careful of bad actors. Make sure to check for incorrect grammar, generic greetings, unrealistic deals and requests for personal information like your password, all of which bad actors may use.
- Sign out on public devices. Other users may be able to access your account on the device afterwards, so make sure to disable options of saving the password and delete browser history and cookies.
- Update software. By updating to the newest software available, current bugs and security compromises may be fixed/improved.
- Enable two-factor authentication. This step, which requires more than one way to verify your identity to secure your account and can help prevent phishing and potential password attacks.
- Be careful of public WiFi. Public WiFi, in some cases, isn’t encrypted, leading to vulnerability of your personal information and websites you are visiting being exposed by bad actors.
- Check your privacy settings. Some apps may have permission to capture data from your camera or microphone that you can switch off.
- Check hyperlinks. Sometimes suspicious emails or messages have links attached. Hover over the link to check if the URL is for the content you are expecting before clicking on it.
- Turn off your Bluetooth when you aren’t using it. Hackers can potentially gain access to your device through Bluetooth and steal personal information.
- Be cautious of HTTP websites. These websites are not secure, so avoid putting in payment information and personal information.